Introduction
I recently went through the effort to migrate a Windows Server 2012 R2 AD FS farm to a Windows Server 2016 AD FS farm. For this exercise the people in charge wanted to maintain the server names and IP addresses. By doing so there is no need for changes in the Kemp Technologies load balancer.
Farm Behavior Level Feature
In Windows Server 2016 ADFS we now have a thing called the Farm Behavior Level (FBL) feature (FBL). It determines the features that the AD FS farm can use. Optimistically you can state that the FBL of a Windows Server 2012 R2 AD FS farm is at the Windows Server 2012 R2 FBL.
The FBL feature and mixed mode now makes a “trick” many used to upgrade a ADFS farm to AD FS Windows Server 2012 R2 organizations without the hassle of setting up a new farm and exporting / importing the configuration possible. looking to upgrade to Windows Server 2016 will not have to deploy an entirely new farm, export and import configuration data. Instead, they can add Windows Server 2016 nodes to an existing farm while it is online and only incur the relatively brief downtime involved in the FBL raise.
We can add a secondary Windows Server 2016 AD FS server to a Windows Server 2012 R2 farm. The farm will continue operating at the Windows Server 2012 R2 FBL. This is “mixed mode” so to speak. There is no need to move all the node to the same version immediately.
As long as you are in mixed mode you don’t get the benefits of the new capabilities and features in Windows Server 2016 ADFS. These are not available.
Administrators can add new, Windows Server 2016 federation servers to an existing Windows Server 2012 R2 farm. As a result, the farm is in “mixed mode” and operates the Windows Server 2012 R2 farm behavior level.
When all Windows Server 2012 R2 nodes have been removed form the farm and all nodes are Windows Server 2016 you can raise the FBL level. This results in the new Windows Server 2016 ADFS features being enabled and ready for configuration and use.
The Migration Path Notes
WARNING
You cannot in place upgrade a Windows Server 2012 R2 ADFS Farm node to Windows Server 2016. You will need to remove it from the farm and replace it with a new Windows Server 2016 ADFS node.
Note
In this migration we are preserving the node names and IP addresses. This means the load balancer needed no configuration changes. So in that respect this process is different from what is normally recommended.
This is a WID based deployment example. You can do the same for an SQL based deployment.
The FBL approach is only valid for a migration from Windows Server 2012 AD FS to Windows Server 2016 AD FS. A migration from AD FS 2.0 or 2.1 (Windows Server 2008 R2 or Windows Server 2012) requires the use of the Export-FederationConfiguration and Import FederationConfiguration as before.
Also see https://technet.microsoft.com/en-us/windows-server-docs/identity/ad-fs/overview/ad-fs-2016-requirements
Step by Step
-
Start with the secondary nodes. For each of them make sure you have the server name and the IP configuration.
-
Make sure you have the Service Communications SSL cert for your AD FS and the domain or managed service account name and password.
- Make sure you have an ADFS configuration backup and also that you have a backup or an export (cool thing about VMs) of the VMs for rapid recovery if needed.
Remove the ADFS role via Server management
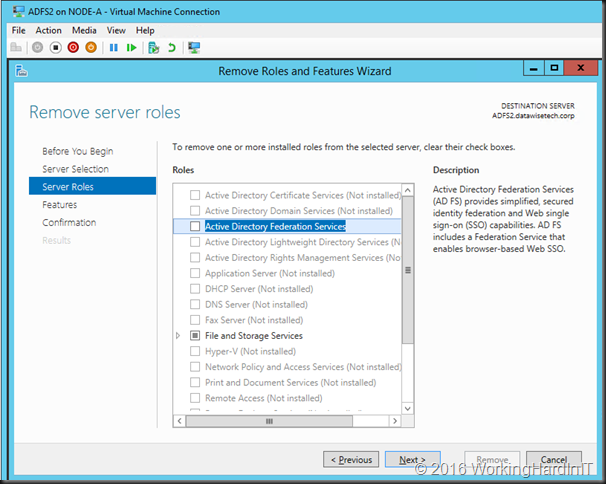
- Shut down the VM
- Edit the setting and remove the OS VHDX. Delete the file (you have a backup/export)
- Copy your completely patched and syprepped OS VHDX with Windows Server to the location for this VM. Rename that VHDX to something sensible like adfs2disk01.vhdx.
- Edit the settings and add the new sysprepped OS VHDX to the VM. Make sure that the disk is 1st in the boot order.
- Start the VM
- Go through the mini wizard and log in to it.
- Configure the NIC with the same setting as your old DNS Server
- Rename the VM to the original VM name and join the domain.
- Restart the VM
- Login to the VM and Install ADFS using Add Roles and Features in Server Manager
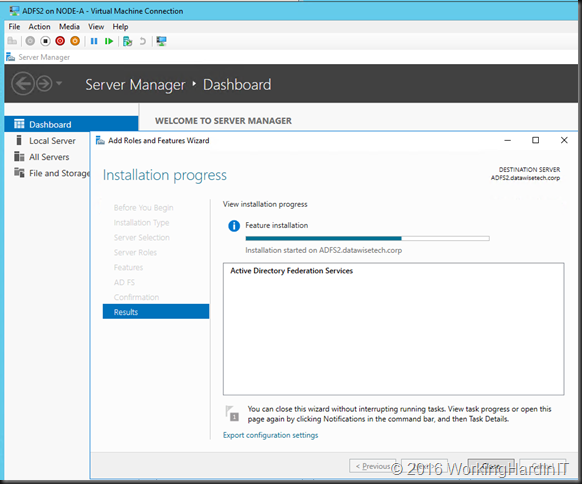
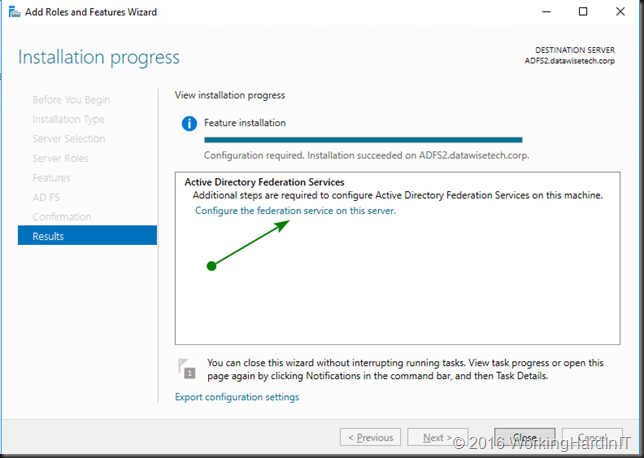
- Select to add the node to an existing federation farm
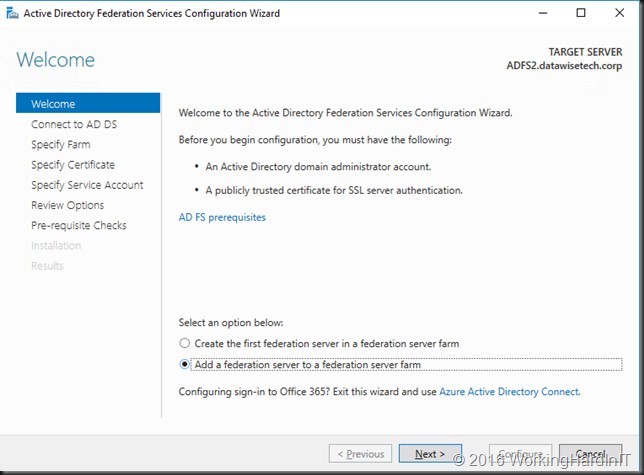
- Make sure you have an account with AD admin permissions
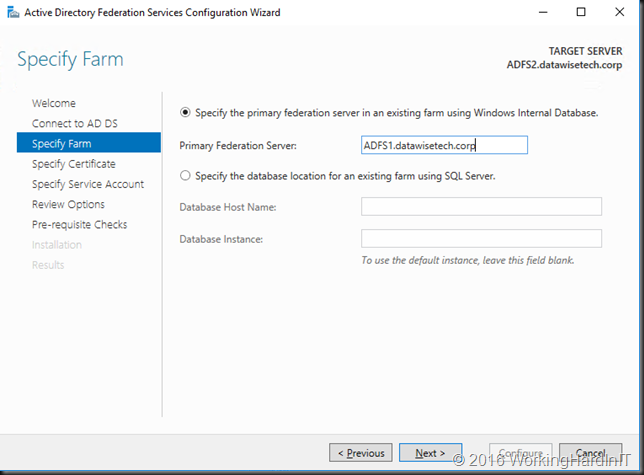
- Tell the node what primary federation server is
- Specify the ADFS Service account and its password
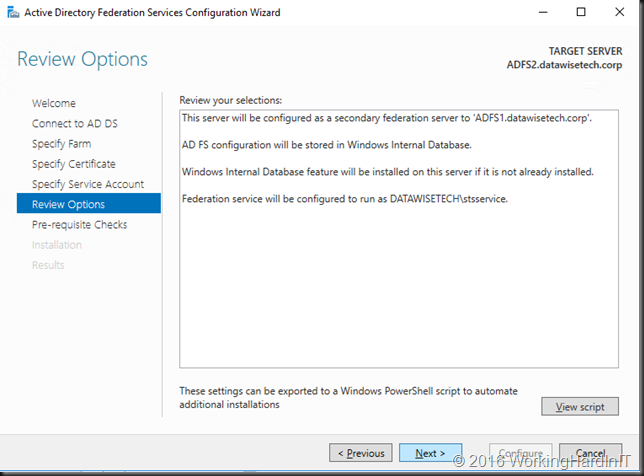
- If any prerequisites don’t work out you’ll be notified, we’re good to go!
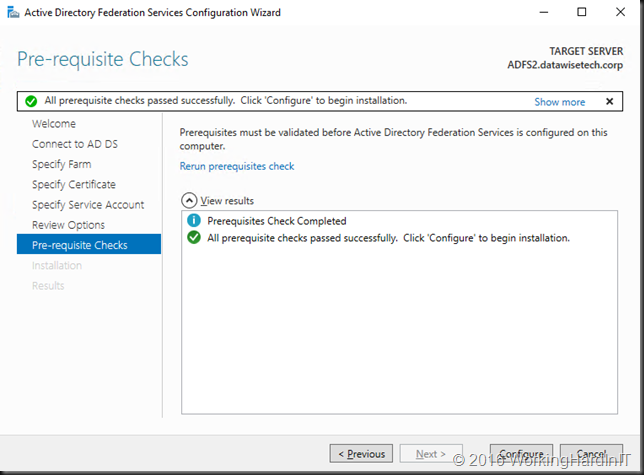
- Let the wizard complete all it steps
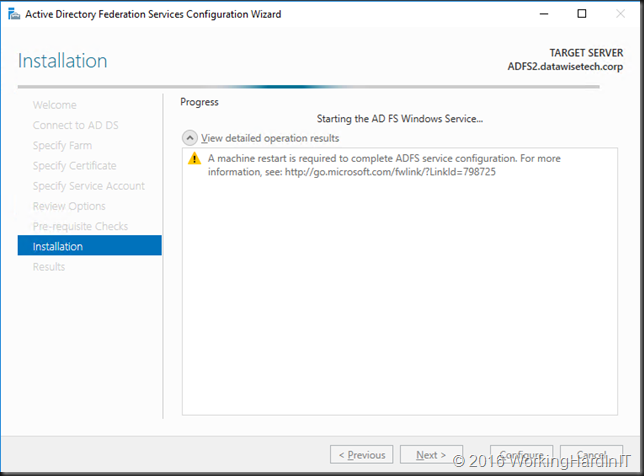
- When the configuration is done you need to restart the VM to complete adding the node to the ADFS farm.
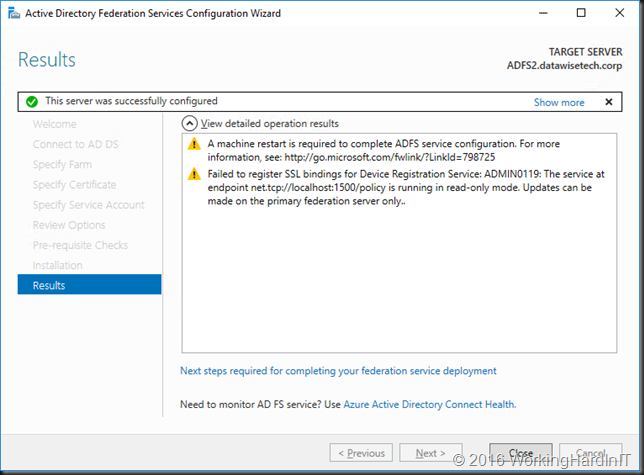
- Restart your VM and log back in. When you open up ADFS you’ll see that this new Windows Server 2016 node is a secondary node in your ADFS Farm.
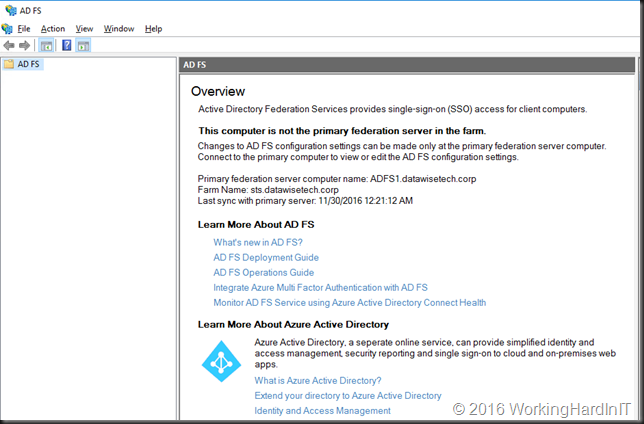
- Note that from a load balancer perspective nothing has changed. They just saw the node go up and down a few times; if they were paying attention at all that is.
- Now repeat the entire process for all you secondary ADFS Farm nodes. When done we’ll swap the primary node to one of the secondary nodes. This is needed so you can repeat the process for the last remaining node in the farm, which at that time needs to be a secondary node. In the example of our 2 node farm we swap the roles between ADFS1 and ADFS2.
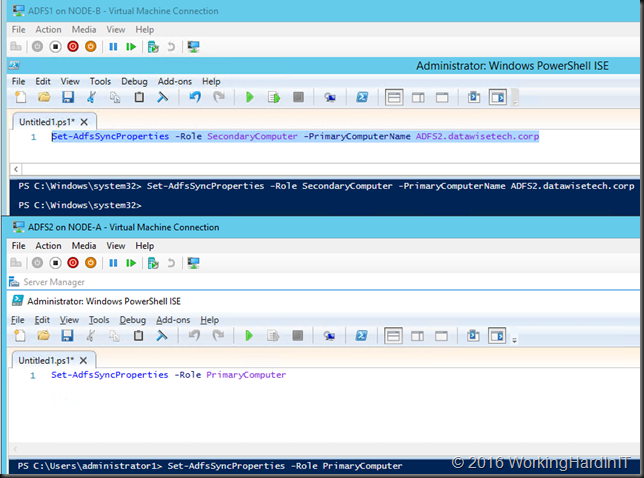
- Verify that ADFS2 is the primary node and if so, repeat the migration process for the last remaining node (ADFS1) in our case.
- Once that’s been completed we swap them back to have exactly the same situation as before the migration.
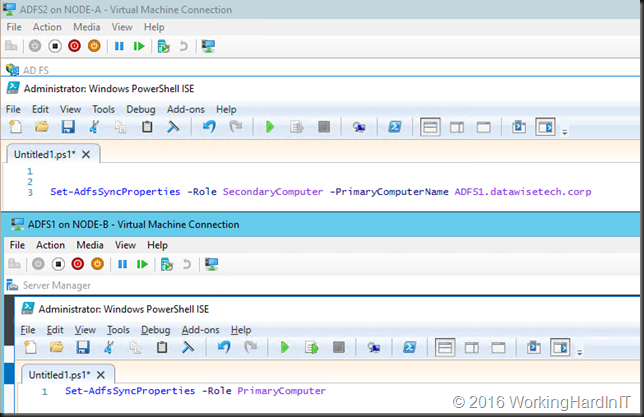
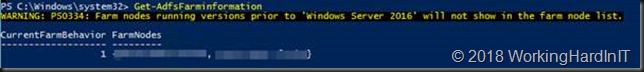
- On the primary node run Get-AdfsFarmInformation (a new cmdlet in Windows Server 2016 R2).
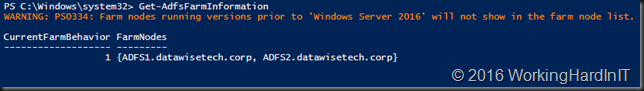
- You’ll see that our current farm behavior is 1 and our 2 nodes (all of them Windows Server 2016) are listed. Note that any nodes still on Windows Server 2012 R2 would not be shown.
WARNING: to raise the FBL to Windows Server 2016 your AD Schema needs to be upgraded to at least Windows Server 2016 version 85 or higher. This is also the case form new AD FS farm installations which will be at the latest FBL by default. My environment is already 100% on Windows Server 2016 AD. So I’m good to go. If yours is not, don’t forget to upgrade you schema. You don’t need to upgrade your DC’s unless you want to leverage Microsoft Password authentication, then you need al least 1 Windows Server 2016 domain controller. See https://technet.microsoft.com/en-us/windows-server-docs/identity/ad-fs/overview/ad-fs-2016-requirements
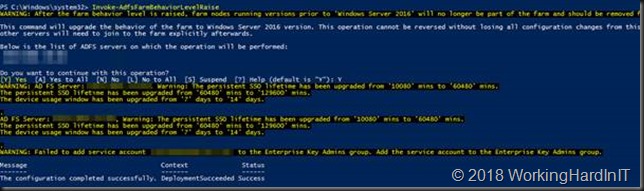
- As we know all our nodes are on Windows Server 2016 we can raise our Farm Behavior Level (FBL) by running Invoke-AdfsFarmBehaviorLevelRaise
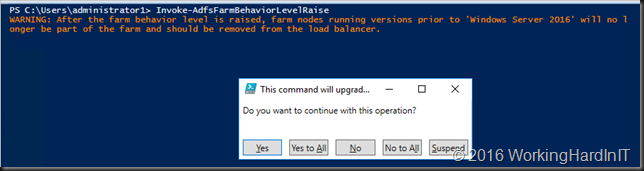
- Just let it run it has some work to do including creating a new database.
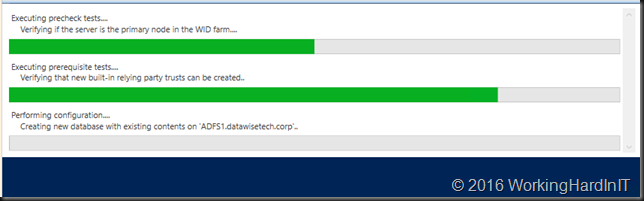
- It will tell you when it’s done and point out changes in the configuration.
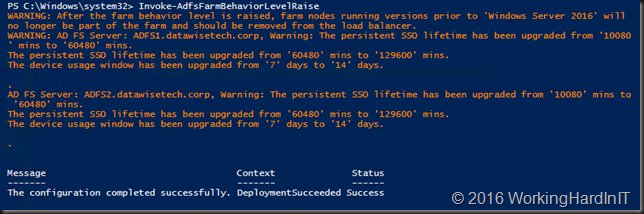
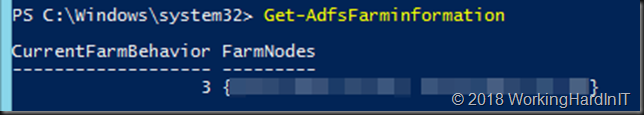
- Now run Get-AdfsFarmInformation again
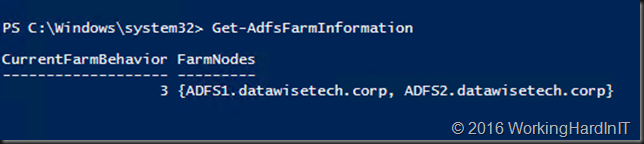
- Note that the current farm behavior is 3 and our 2 nodes (all of them Windows Server 2016) are listed. Note that if any nodes had still been on Windows Server 2012 R2 they would have been kicked from the farm and should be removed form the load balancer.
PS: with some creativity and by having a look at my blog on https://blog.workinghardinit.work/2016/11/28/easily-migrating-non-ad-integrated-dns-servers-while-preserving-server-names-and-ip-addresses/ You can easily figure out how to add some extra steps to move to generation 2 VMs while you’re at it if you don’t use these yet.