Instead of testing Windows Server 2016 TPv4 a bit more during “slow” hours we got distracted from that a bit CryptoWall 3.0 strikes to close for Comfort. Last week we, my team and I, had to distinct displeasure of having to tackle a “ransomware” infection inside a business network. Talk about petting a burning dog.
We were lucky on a few fronts. The anti malware tools got the infection in the act and shut it down. We went from zero and 100 miles per hour and had the infected or suspect client systems ripped of the network and confiscated. We issue a brand new imaged PC in such incidents. No risks are taken there.
Then there was a pause … anything to be seen on the anti malware tools? Any issues being reported? Tick tock … tick tock … while we were looking at the logs to see what we were dealing with. Wait Out …
Contact! The first reports came in about issues with opening files on the shares and soon the service desk found the dreaded images on subfolders on those shares.
Pucker time as we moved to prevent further damage and started an scan & search for more encrypted files and evidence of damage. I’m not going to go into detail about what, why, when and how. As in all fights you have to fight as you are. No good wishing for better defenses, tools, skills or training. At that moment you do what you think you need to do to contain the situation, clean up, restore data and hope for the best.
What can I say? We got lucky. We did our best. I’d rather not have to do that again. We have multiple types of backup & restore capabilities and that was good. But you do not want to call all data lost beyond a point and start restoring dozen of terabytes of corporate data to a last know good without any insight on the blast radius and fall out of that incident.
The good thing was our boss was on board to do what needed and could be done and let us work. We tried to protect our data while we started the cleanup and restores where needed. It could have been a lot uglier, costlier and potentially deadly. This time our data protection measures saved the day. And at least 2 copies of those were save from infection. Early detection and response was key. The rest was luck.
Crypto wall moves fast. It attempts to find active command and control infrastructure immediately. As soon as it gets it public key from the command and control server that it starts using to encrypt files. The private key securely hidden behind “a pay wall” somewhere in a part of the internet you don’t want to know about. All that happens in seconds. Stopping that is hard. Being fast limits damage. Data recovery options are key. Everyday people are being trapped by phishing e-mails with malicious attachments, drive by downloads on infected website or even advertisement networks.
Read more on CryptoWall 3.0 here https://www.sentinelone.com/blog/anatomy-of-cryptowall-3-0-a-look-inside-ransomwares-tactics/ Details on how to protect and detect depend on your anti malware solution. It’s very sobering, to say the least.
It makes me hate corporate apps that require outdated browsers even more. Especially since we’ve been able to avoid that till now. But knowing all to well forces are at work to introduce those down grade browsers with “new” software. Insanity at its best.

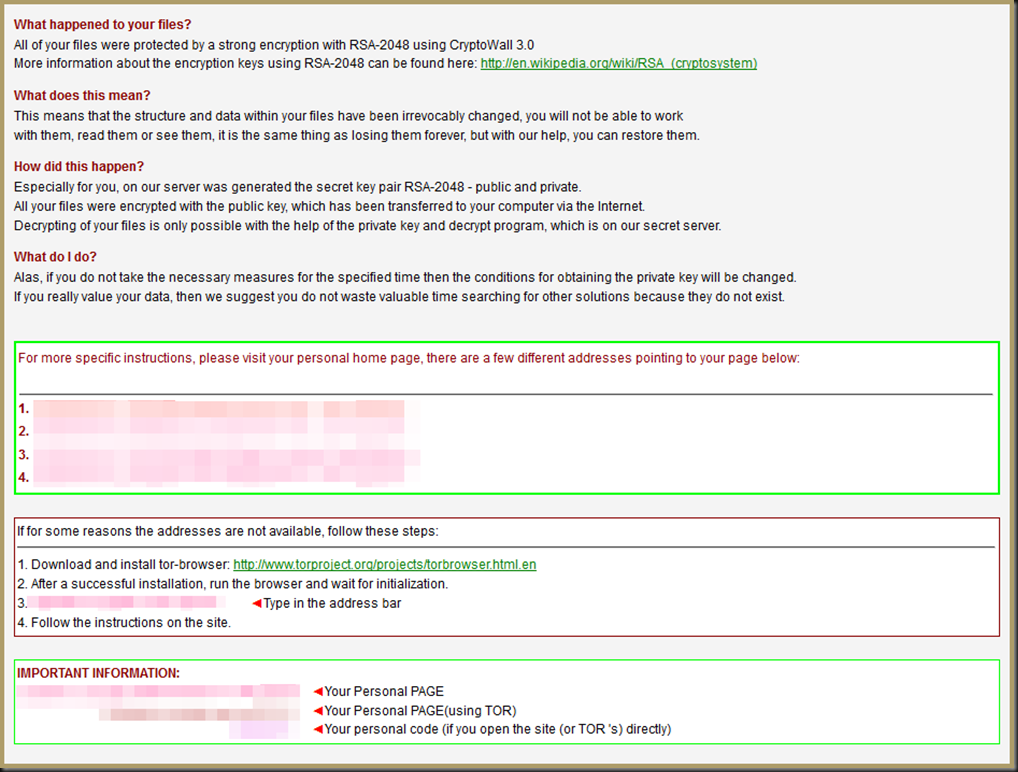
This is straight conjecture from my last encounter with CryptoWall, but I had an infection on a single PC with Shared network drives not getting touched.
Keeping in mind there are hundreds of different cryptowall variants, it could be that I had an older one, however, it DID write the .txt / .rtf / .png files to the root of all my shares (those notes that tell you how to decrypt).
From my investigation, the reason it was unable to touch anything on the server shares was that I had my security ACLs / Share ACLs limited to Modify. This doesn’t make the most sense, as all the users could create new documents, edit current ones, save new ones, save edited ones, etc, yet CryptoWall was unable to take any of the files and encrypt them. I need to test this in my lab more to confirm though.
Another piece that can be done to limit if not remove the threat of ransomware like this (it is only going to be on the rise), is to use a smart edge router / firewall / UTM. On my end I recommend Sophos, as their Botnet / CnC detection system has saved multiple clients from having anything get encrypted. These are extremely efficient at stopping all but the newest ransomware, as it blocks their ability to communicate with the command and control server, and thus never gets a key to encrypt. This software won’t encrypt until it gets that key since generating the key on the workstation itself makes it infinitely easier for AV vendors to create a decryption tool / reverse engineer the software and find holes in the generation of the security key.
Biggest success rate on my end that I have seen the ransomeware creators use? RESUMES
Think about it for a second – I put a post on Craigslist or Monster saying I am hiring for position X. As a bad actor, all i have to do is create a very thin identity (gmail address, first and last name from linkedin / facebook), and then I can send my crafted resume file. This can also be automated very easily with a web crawler to parse e-mails / position titles / etc to make the resume look more legit and get a higher open ratio. But lets be honest – if you are an employee who posted for a job, you will be opening close to 100% of the resumes you get…
Well, this year we migrated from IE8 to IE11! 🙂 Hope the sucker doesn’t get us…